Seamlessly use Github using SSH keys

GitHub, along with many other code versioning platforms (such as Bitbucket), provides a secure and efficient way to manage and collaborate on projects. By utilizing SSH keys, you can seamlessly interact with your repositories, enabling secure authentication without the need for passwords.
By leveraging SSH's config file, you can simplify repository interaction without having to specify the SSH URL each time. This comprehensive guide will walk you through setting up SSH configurations to streamline your GitHub experience. After completing this guide, you will never have to struggle with your repository access or compromising security.
Step 1: Generating SSH Key Pair
- Open your terminal.
- Generate an SSH key pair using the
ssh-keygencommand:
ssh-keygen -t rsa -b 4096 -C "[email protected]"Replace [email protected] with your email address.
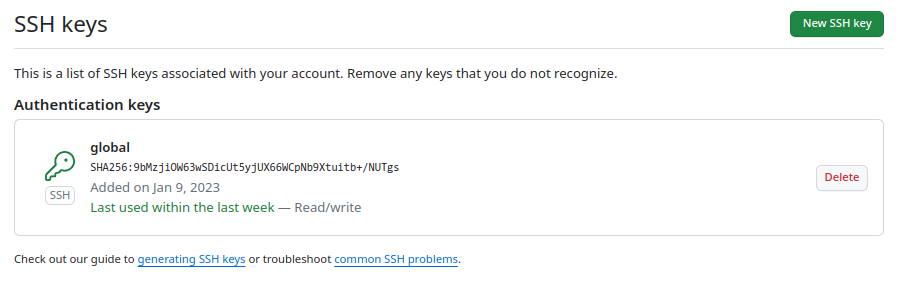
Step 2: Adding SSH Key to GitHub
- Display the public key using
cat ~/.ssh/id_rsa.pub. - Copy the entire content of the public key.
- Open your GitHub account in a web browser.
- Navigate to Settings > SSH and GPG keys > New SSH key.
- Paste the copied public key into the "Key" field and provide a descriptive title.
- Click Add SSH key to save it.
Step 3: Configuring SSH for GitHub
- Open or create the SSH config file:
nano ~/.ssh/config
If the file doesn't exist, create it (nano or vim creates it automatically on write).
- Add GitHub configurations:
Host github.com
HostName github.com
IdentityFile ~/.ssh/id_rsa
Replace ~/.ssh/id_rsa with the path of your private key file
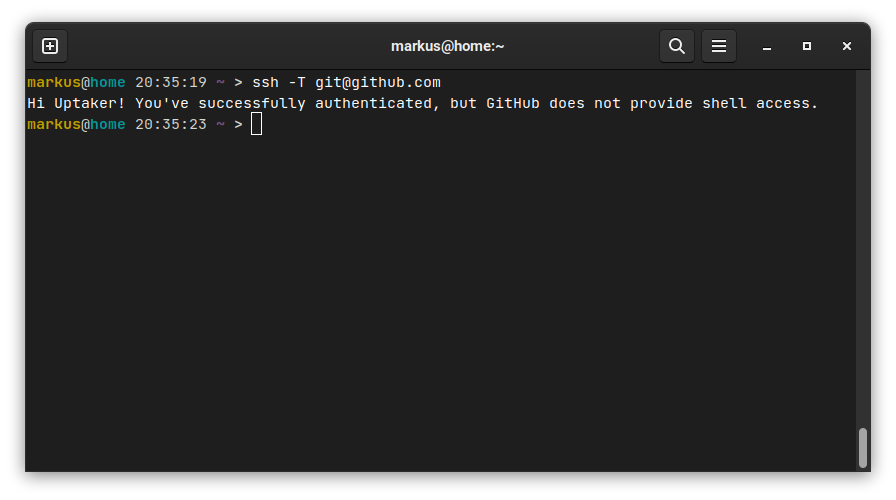
Step 4: Testing the Connection
Verify the SSH connection to GitHub:
ssh -T [email protected]
You should receive a success message indicating a successful SSH connection to GitHub.
That's it!
You can now use the SSH option to clone and work with your Github repository.
Make your existing local repositories compatible
Normally, you could simply push any changes and reclone, but you can also manually tell git to change the origin URL.
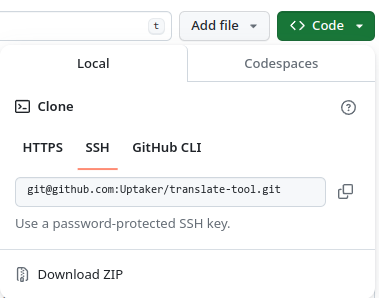
Let's use my Translate Tool project as an example and see how to change that.
https://github.com/Uptaker/translate-tool.gitHTTPS URL
[email protected]:Uptaker/translate-tool.gitGit URL
- Navigate to your repository.
- Set the remote URL to use SSH:
git remote set-url origin [email protected]:Uptaker/translate-tool.git
Replace Uptaker/translate-tool.git with your actual GitHub repository URL.
- You can now interact with your repository normally as you did before.
Conclusion
By configuring SSH and utilizing the SSH config file, you've streamlined the process of interacting with GitHub repositories. This setup enables seamless and secure authentication, allowing you to manage your repositories efficiently.
Hope this article helped, and that you've learned something new!
Learn more
We've used the SSH config to configure this automatically. Learn its other uses as well to become more productive and secure in this short walkthrough.








